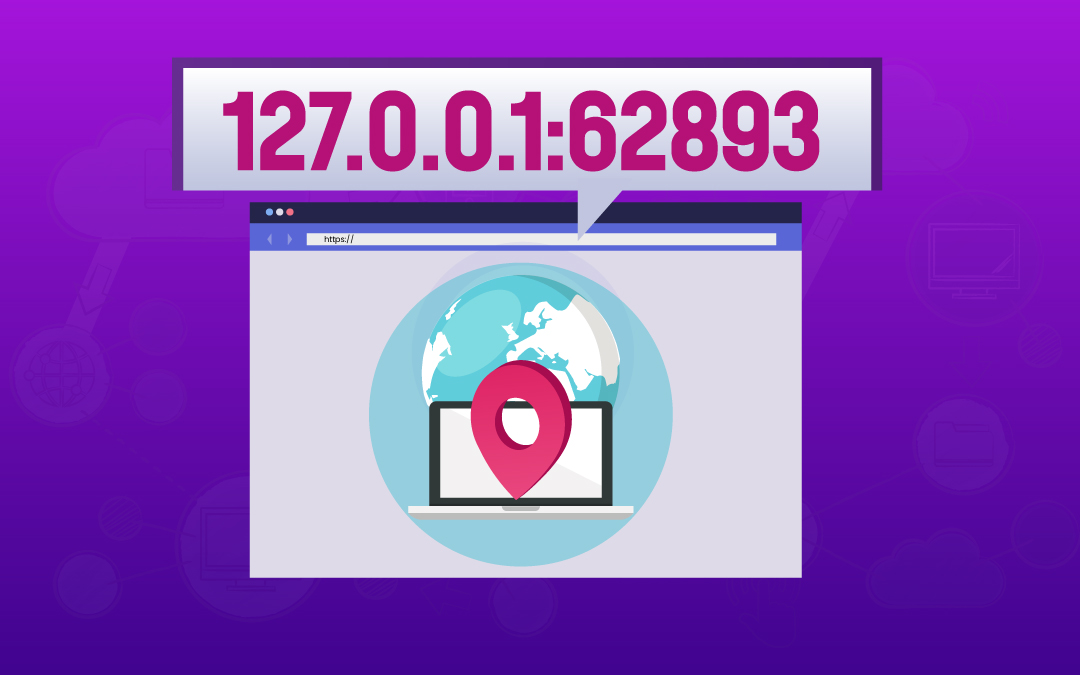
127.0.0.1 is an IP address known as a loopback address which enables a computer system to exchange packets directly with itself - useful for testing local networks and troubleshooting purposes. 62893 is a dynamic port number used for temporary communication in custom applications. There is no standard service assigned to port 62893, developers use it for testing purposes.