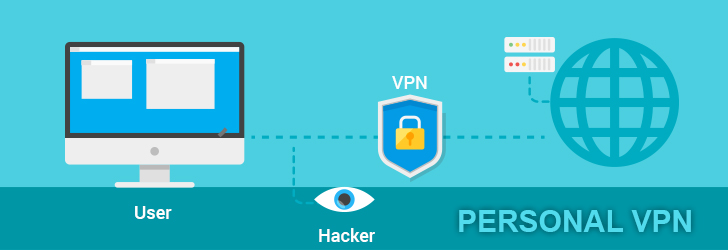
A VPN, or Virtual Private Network, is used to securely connect to another network via a public or a private network. A VPN creates a private network within a broader network, thus providing added-security using encryption and network tunneling mechanisms. A VPN is like a bridge that connects two islands (here, LANs) to establish an private, secure and more reliable connection between the two islands (here, local networks). This helps ease security and privacy issues; since the data transmitted over a VPN is encrypted and unreadable to general Internet community. There are two types of VPNs, namely remote-access VPN and site-to-site VPN.
Remote Access VPN
A remote access VPN, also known as point-to-point (PPP) VPN allows individual users to establish a secure connection to a remote server. A VPN user joins the private network offered by VPN software and freely accesses the secure resources on that network as if the user is directly connected. The remote-access VPN requires two components: a Remote Access Server and VPN client software that enables the user to establish and maintain a VPN connection. It is required to establish a tunneled connection to a NAS, indicated using an internet address, while it also helps manage the encryption needed for a secure connection.Site-to-Site VPN
A site-to-site VPN helps establish a secure connection between two sites or locations, over a public network such as the Internet. A site-to-site VPN may extend two networks into a single network (Intranet VPN), or interconnect two separate networks while maintaining its locality (Extranet VPN).
VPN Tunneling
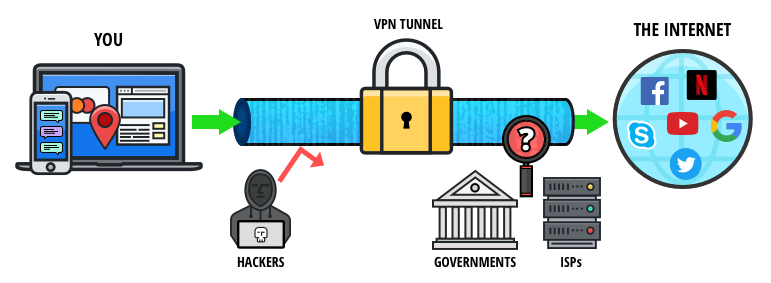
A VPN uses the mechanism of tunneling to create a private network across the Internet. Tunneling is a network technology that involves the process of layering of capsules, known as encapsulation. In this process, series of packets are created by breaking down each data file, and an entire packet is placed within another outer packet before it is sent and received across the computers. Movement of the encrypted packet within an outer packet, also known as a virtual tunnel, ensures secured transfer.
The VPN technology makes use of a tunnel management protocol mechanism that helps create, maintain, and terminate the tunnel, which enables seamless data transfer. Meanwhile, devices or computers that are present at both ends of the tunnel are known as tunnel interfaces, which facilitate the process of encapsulation and reopening of outgoing and incoming packets respectively.
Advantages of VPN
There are several advantages of using a VPN service ranging from bypassing internet censorship to accessing global content without any geo-restrictions, added internet security, and anonymous browsing. Most basic properties of VPNs that distinguish them from other personal networks are as below:
Security: VPNs provide high security, thus protecting users’ data from being hacked, especially on a public network.
Reliability: VPNs are accompanied with high-reliability standards, providing similar quality of connection for each user while handling multiple and simultaneous connections.
Scalability: VPNs can easily be expanded to accommodate more users and different locations when compared to leased lines. This enables the expansion of in-house VPN services without the need for replacement of the technology on the whole.
Flexibility: VPNs provide a flexible option for remote offices to use a common professional intranet over an existing connection, as though they are directly connected to the internet.
Besides the notable features described above, a personal VPN offers following advantages.
- A VPN enables users to connect to remote servers located in various parts of the globe using chosen IPs at any point in time. This anonymous browsing helps prevent hackers from intruding into the personal network, as well as sharing files and data over an encrypted medium.
- A VPN helps maintain network security and also facilitate anonymous browsing from anywhere in the world with an IP address of any chosen location.
- Several countries are now implementing Internet Censorship as part of the national security laws. This includes content regulation, filtering and blocking policies to suppress the use of the free internet. Hence, number of people are opting for VPN services to make use of anonymous browsing feature to overcome the issues associated with monitored internet usage.
- A VPN provides ways to bypass the monitoring mechanism and get exposed to global content on the internet. A VPN service is the safest way to browse the internet and unblock some of the websites known as geo-restricted sites, which are not accessible within specific geographical regions.
- Mobile VPNs facilitate reliable connections, and are used for seamless roaming across networks, and within wireless coverage areas, without losing VPN connectivity or application sessions.
- Given the increasing need for secure and private browsing, several router manufacturers (such as Cisco, Linksys, Asus, and Netgear) are deploying VPN connectivity on routers by manufacturing routers with built-in VPN clients.
- This not only facilitates additional security and encryption of data transmission by using various cryptographic techniques but also allows any connected device (smart TVs and gaming consoles among others) to use the VPN network while it is enabled.
- Assuring high standards of privacy and anonymous browsing options, VPNs help safeguard the users from hackers and data thefts. Hence, new and better technologies are being developed over time to use in networks, in order to improve the features of existing VPNs.
Top VPN providers in the market
In order to use above mentioned privileges of secured and anonymous internet browsing, there is a need for a best-of-its-kind VPN service subscription. There are a few VPN service providers in the market, however choosing a provider needs a lot of research. To make this job easier, we have compiled a list of VPN providers that are top-rated in the current market. We recommend our readers to explore the VPN services offered by Vypr VPN to hide IP and protect your identity online.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.







Comments (1)
I please want to hide my IP address Im being hacked
Apr 24, 2020 at 03:34 AMPlease visit hide IP address to discover ways to hide your IP address.