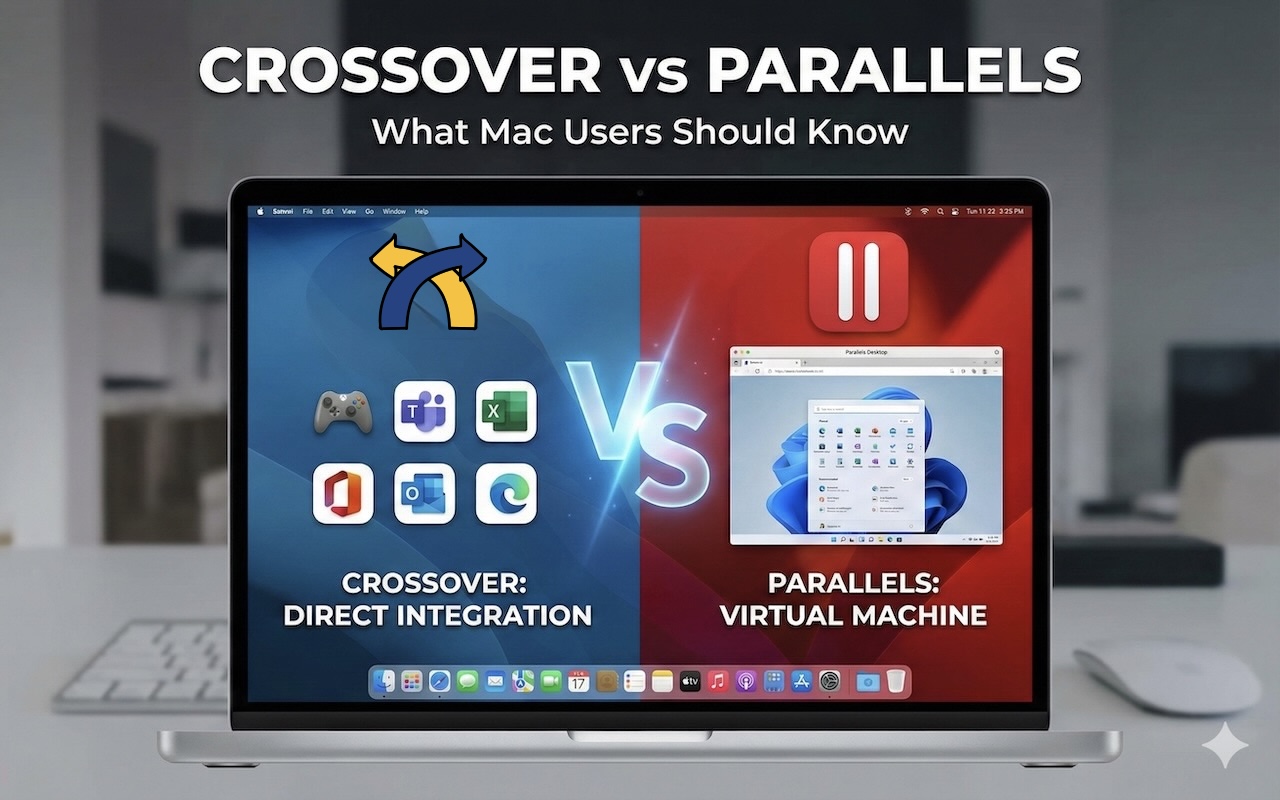
With other native applications, many Mac owners look for ways to run them on their systems. The most common ones are Crossover and Parallels. Each of these tools has a very different approach, with its own set of pros and cons. Knowing the differences between them helps in choosing the right one as per requirements.