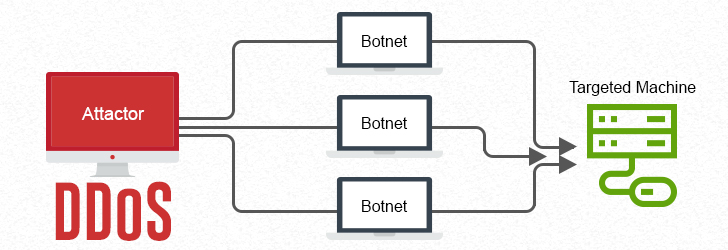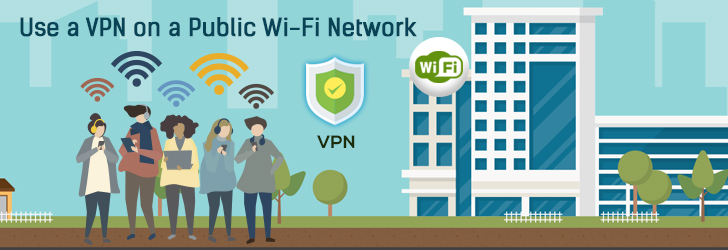
Unsecured public Wi-Fi is everywhere; most restaurants, airports, malls, and coffee shops offer your device a free connection while you shop, travel, or drink copious quantities of caffeine to power your day. Sometimes, public Wi-Fi networks are a user's only option, despite the risky nature of its "unsecure" status. But connecting your laptop or smartphone on public Wi-Fi can be problematic for many reasons, which typically fall under one of two categories: Security and Access.
[..]
Read more...